For background on this particular project, please visit How to Prevent Your Business from Getting Hacked.
Situation ...
A closely-held company provides various financial, accounting, investment management, and tax services to its clients. Information systems play a critical role in delivering these services.
Problem ...
This company outsources much of its information systems function. Executives and management believed that this arrangement was working well, and that the network and certain applications were being adequately maintained and protected under the guidance of their network service provider. Top executives, however, wanted to validate this belief, both for their own peace of mind, as well as to be able to answer questions from clients, auditors, and bankers, should they arise.
Solution ...
Our client retained us to assess the various network, infrastructure, and security technologies and techniques in use at the company. Our approach was to:
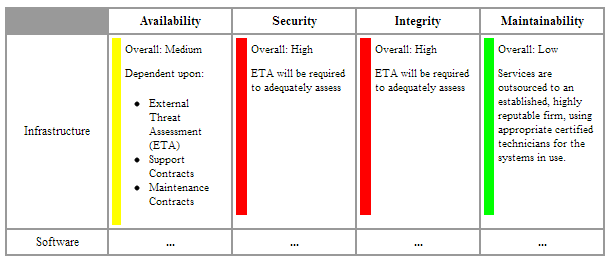
- Perform an Initial Risk Assessment, to assess the level of risk (High, Medium, or Low),
in the areas of... ...in terms of... - Infrastructure
- Software
- People
- Procedures, and
- Data.
- Availability
- Security
- Integrity, and
- Maintainability.
- Assess internal threats from procedural gaps or weaknesses, lack of training, or maintenance shortcomings.
- Work jointly with a business partner specializing in our client’s industry to conduct an External Threat Assessment.
- Perform substantive tests for areas identified as "High"; risk to assess whether identified risks are adequately addressed or have appropriate alternative controls.
- Summarize the results of tests and our recommendations in an Engagement Report.
An excerpt from the Initial Risk Assessment matrix – jointly discussed and assessed by management and us – provided the basis for the overall scope of the project.
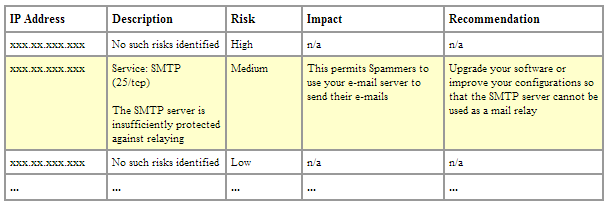
One section from the External Threat Assessment report details risks associated with external IP addresses.
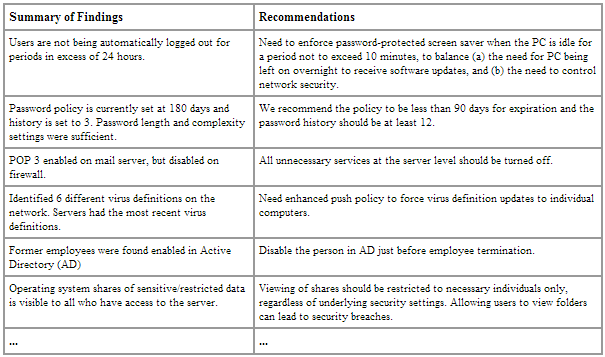
One part of our Engagement Report presents key findings and recommendations.
Results and Benefits ...
Several areas that management had not truly assessed were shown to have better security than believed. The internal and external threat assessments identified specific steps required to mitigate several remaining risks. Upon completion of these steps, management responsible for the Information Systems function will be better able to assess potential risks, through knowledge and techniques learned during this engagement.
Conclusion ...
Our client decided to proactively assess and address risks in their systems environment, communicating to employees that systems security is important, and providing their clients and other relevant parties improved confidence in the controls protecting sensitive personal financial information.
For Further Information ...
To discuss how we could help your business, please call us at 336.297.4200 to schedule a no-obligation consultation.